Top Spam Botnet, “Grum,” Unplugged
Nearly four years after it burst onto the malware scene, the notorious Grum spam botnet has been disconnected from the Internet. Grum has consistently been among the top three biggest spewers of junk email, a crime machine capable of blasting 18 billion messages per day and responsible for sending about one-third of all spam.
The takedown, while long overdue, is another welcome example of what the security industry can accomplish cooperatively and without the aid of law enforcement officials. Early press coverage of this event erroneously attributed part of the takedown to Dutch authorities, but police in the Netherlands said they were not involved in this industry-led effort.
The Grum ambush began in earnest several weeks ago at the beginning of July, following an analysis published by security firm FireEye, a Milpitas, Calif. based company that has played a big role in previous botnet takedowns, including Mega-D/Ozdok, Rustock, Srizbi.
Atif Mushtaq, senior staff scientist at FireEye, said the company had some initial success in notifying ISPs that were hosting control networks for Grum: The Dutch ISP Ecatel responded favorably, yanking the plug on two control servers. But Mushtaq said the ISPs where Grum hosted its other control servers — networks in Russia and Panama — proved harder to convince.
“I sent the Russian CERT [computer emergency response team] abuse notices about these command and control networks on Russian ISPs and they sent us a one-liner email saying ‘These are not our IPs,” Mushtaq said, referring to the Internet addresses of the Grum control servers that were operating on Russian ISPs. But FireEye found success in appealing to the Russian ISP’s upstream Internet provider, which severed its connection to some 256 Internet addresses in the area of the Russian Grum controllers.
The Panamanian hosting firms followed suit, but the takedown effort suffered a temporary setback when the Grum botmaster(s) set up backup control networks at ISPs in Ukraine. But they, too, were soon disabled, leaving the infected Grum bots without any control networks telling them what to do.
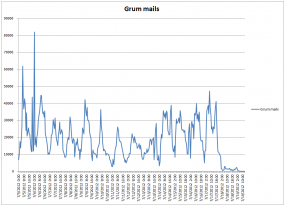
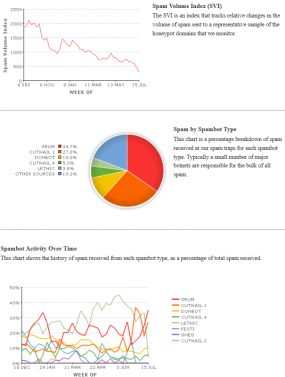
“According to data coming from Spamhaus, on average, they used to see around 120,000 Grum IP addresses sending spam each day, but after the takedown, this number has reduced to 21,505,” Mushtaq wrote in a follow-up blog post. “I hope that once the spam templates expire, the rest of the spam with fade away as well.”
And fade away it has, at least according to data recorded by Symantec’s MessageLabs (see graphic at the top of this post).
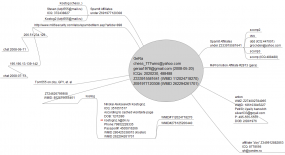
It remains unclear whether the individual(s) responsible for Grum will ever be brought to justice. Grum has long been associated with spam promoting rogue Internet pharmacies, and in February, I published a lengthy analysisof data leaked from two of the largest pharmacy spam affiliate programs showing the earnings and possible identity information of the Grum botmaster. That analysis tied Grum’s activities and profits back to a hacker who used the nickname “Gera,” and whose payment accounts were linked to a Russian named Nikolai Alekseevich Kostogryz (see graphic below for more details on Gera).
At that time, Grum was the world’s most active spam botnet, according to statistics maintained by M86 Security Labs, a company since acquired by Trustwave. Very soon after my investigative piece on Grum was published, KrebsOnSecurity.com was the target of a rather large distributed denial of service (DDoS) attack. I’ve recently learned that the attack was launched by the Grum botnet, suggesting that the findings were a little too close to home for the Grum botmaster(s).
Brett Stone-Gross, a senior security researcher for Atlanta-based Dell SecureWorks, analyzed a copy of the Grum malware from that time and found that it was instructing all infected systems to visit 94.228.133.163 (the IP address for krebsonsecurity.com). The nonexistent filename that the Grum bots were told to fetch from my site was “fuckingyou^^/9590899.php”.
The takedown, while long overdue, is another welcome example of what the security industry can accomplish cooperatively and without the aid of law enforcement officials. Early press coverage of this event erroneously attributed part of the takedown to Dutch authorities, but police in the Netherlands said they were not involved in this industry-led effort.
The Grum ambush began in earnest several weeks ago at the beginning of July, following an analysis published by security firm FireEye, a Milpitas, Calif. based company that has played a big role in previous botnet takedowns, including Mega-D/Ozdok, Rustock, Srizbi.
Atif Mushtaq, senior staff scientist at FireEye, said the company had some initial success in notifying ISPs that were hosting control networks for Grum: The Dutch ISP Ecatel responded favorably, yanking the plug on two control servers. But Mushtaq said the ISPs where Grum hosted its other control servers — networks in Russia and Panama — proved harder to convince.
“I sent the Russian CERT [computer emergency response team] abuse notices about these command and control networks on Russian ISPs and they sent us a one-liner email saying ‘These are not our IPs,” Mushtaq said, referring to the Internet addresses of the Grum control servers that were operating on Russian ISPs. But FireEye found success in appealing to the Russian ISP’s upstream Internet provider, which severed its connection to some 256 Internet addresses in the area of the Russian Grum controllers.
The Panamanian hosting firms followed suit, but the takedown effort suffered a temporary setback when the Grum botmaster(s) set up backup control networks at ISPs in Ukraine. But they, too, were soon disabled, leaving the infected Grum bots without any control networks telling them what to do.
“According to data coming from Spamhaus, on average, they used to see around 120,000 Grum IP addresses sending spam each day, but after the takedown, this number has reduced to 21,505,” Mushtaq wrote in a follow-up blog post. “I hope that once the spam templates expire, the rest of the spam with fade away as well.”
And fade away it has, at least according to data recorded by Symantec’s MessageLabs (see graphic at the top of this post).
It remains unclear whether the individual(s) responsible for Grum will ever be brought to justice. Grum has long been associated with spam promoting rogue Internet pharmacies, and in February, I published a lengthy analysisof data leaked from two of the largest pharmacy spam affiliate programs showing the earnings and possible identity information of the Grum botmaster. That analysis tied Grum’s activities and profits back to a hacker who used the nickname “Gera,” and whose payment accounts were linked to a Russian named Nikolai Alekseevich Kostogryz (see graphic below for more details on Gera).
At that time, Grum was the world’s most active spam botnet, according to statistics maintained by M86 Security Labs, a company since acquired by Trustwave. Very soon after my investigative piece on Grum was published, KrebsOnSecurity.com was the target of a rather large distributed denial of service (DDoS) attack. I’ve recently learned that the attack was launched by the Grum botnet, suggesting that the findings were a little too close to home for the Grum botmaster(s).
Brett Stone-Gross, a senior security researcher for Atlanta-based Dell SecureWorks, analyzed a copy of the Grum malware from that time and found that it was instructing all infected systems to visit 94.228.133.163 (the IP address for krebsonsecurity.com). The nonexistent filename that the Grum bots were told to fetch from my site was “fuckingyou^^/9590899.php”.
rtechinsane,icodesource,SEO,SEO Tips,SEO Backlinks,SEO content,SEO tricks,SEO Engine,codes,gadgets,iphones,ipad,4G phones,geeks,reviews,database,DBMS,


0 comments:
Post a Comment