Last week,
Microsoft Corp. made headlines when it scored an unconventional if not unprecedented legal victory: Convincing a U.S. court to let it seize control of a Chinese Internet service provider’s network as part of a crackdown on piracy.
I caught up with Microsoft’s chief legal strategist shortly after that order was executed, in a bid to better understand what they were seeing after seizing control over more than 70,000 domains that were closely associated with distributing hundreds of strains of malware. Microsoft said that within hours of the takeover order being granted, it saw more than 35 million unique Internet addresses phoning home those 70,000 malicious domains.
First, the short version of how we got here: Microsoft investigators found that computer stores in China were selling PCs equipped with Windows operating system versions that were pre-loaded with the “Nitol” malware, and that these systems were phoning home to subdomains at
3322.org. The software giant subsequently identified thousands of sites at 3322.org that were serving Nitol and hundreds of other malware strains, and convinced a federal court in Virginia to grant it temporary control over portions of the dynamic DNS provider.
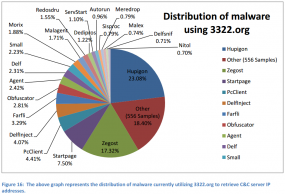
Microsoft was able to do that because – while 3322.org is owned by a firm in China — the dot-org registry is run by a company based in Virginia. Yet, as we can see from the graphic above provided by Microsoft, Nitol infections were actually the least of the problems hosted at 3322.org (more on this later).
To learn more about the outcome of the seizure, I spoke with
Richard Boscovich, a senior attorney with the company’s digital crimes unit (DCU) who helped to coordinate this action and previous legal sneak attacks against malware havens. Our interview came just hours after Microsoft had been cleared to seize control over the 70,000+ subdomains at 3322.org. I asked Boscovich to describe what the company was seeing.
“The numbers are quite large,” he said. “Just a quick view of what we’ve been seeing so far is upwards of 35 million unique IP [addresses] trying to connect with the 70,000 subdomains.”
Certainly IP addresses can be very dynamic — a single computer can have multiple IP addresses over a period of a few days, for example. But even if there were half as many infected PCs than unique IPs that Microsoft observed reporting to those 70,000 domains, we’d still be talking about an amalgamation of compromised PCs that is far larger than any known botnet on the planet today. So how certain was Microsoft that these 35 million unique IPs were in fact infected computers?
“We started identifying what our AV company blocks,” Boscovich explained. “We saw a lot of different types of malware, from keyloggers to
DDoS tools and botnets going back there. Our position would be if you’re reaching out to these 70,000 subdomains, that the purpose would be you’re directed there to be infected or you are already infected with something. And that something was up to 560 or so malware strains we identified [tracing back] to 3322.org.”
COLLATERAL DAMAGE?
Microsoft’s past unilateral actions against malware purveyors and botnets have engendered their share of
harshreactions from members of the security community, and I fully expected this one also would be controversial. I wasn’t disappointed: Writing for Internet policy news site
CircleID, longtime antispam activist
Suresh Ramasubramanian warned that Microsoft’s action would cause “extremely high collateral damage,” both to innocent sites and to ongoing investigations.
“So, in the medium to long term run …all that Microsoft DCU and Mr. Boscovitch have achieved are laudatory quotes in various newspapers and a public image as fearless and indefatigable fighters waging a lone battle against cybercrime,” Ramasubramanian
wrote. “That manifestly is not the case. There are several other organizations (corporations, independent security researchers, law enforcement across several countries) that are involved in studying and mitigating botnets, and a lot of their work just gets abruptly disrupted (jeopardizing ongoing investigations, destroying evidence and carefully planted monitoring).”
Boscovich said Microsoft worked hard to focus its legal request on 3322.org subdomains that appeared to be doing little else than serving as controllers, updaters or data repositories for malware operations. He noted that the 70,000 domains the court granted it control over
were only a small subset (less than 3 percent) of the 2.75 million subdomains currently host at 3322.org.
“There’s always a balancing act,” the Microsoft lawyer told me. “You want to make sure you do it in such a way to minimize collateral damage on legitimate sites. The unique aspect of this action was the great lengths that we went to make sure that we surgically took out and sinkholed 70,000 subdomains out of a domain hosting 2.75 million subdomains total. We developed technology along with
Nominum where we were able to — once a domain was pointed to us — to only take out those 70,000, allowing all of the other subdomains which are beyond the scope of our order to simply resolve and not be impacted.”
Boscovich added that Microsoft and Nominum will be working with Internet service providers to help clean machines seen reporting to the hostile 3322.org sites.
“A lot of people in the security community like to do a lot of research, they like sit on these things and see what’s happening, but sometimes the right thing to do is get to the victims, tell them that they’ve been victimized, tell them that they’re victimizing others, and help clean them up,” he said.
Other luminaries in the security research space expressed surprise at the breadth of Microsoft’s latest legal action, but said it was too soon to say how much of an impact it would have on the malware ecosystem.
Dan Hubbard, chief technology officer at
OpenDNS, said his firm has been blocking all 2.75 million subdomains at 3322.org for almost two years.
“We very rarely get complaints, and even today we see 1.1 million requests [attempting to go to] 3322.org with zero complaints,” Hubbard said. “The vast majority of it is not good.”
But he said he wonders what Microsoft is going to do with all of the sensitive information flowing through the sinkholed 3322.org domains. As I noted in
my previous piece, subdomains at 3322.org have long been associated with targeted malware used in espionage attacks against U.S. and other Western corporations.
“There is going to be quite a bit of sensitive information that’s coming across the flow, from credit card details to proprietary company records,” Hubbard said. “It will be interesting to know what are the bounds around that, what they do with that data, and are they going to inform companies that are impacted.”
Joe Stewart, a senior security analyst with
Dell SecureWorks, agreed, calling the scope of the interception order “unprecedented.”
“It’s a little bit surprising that Microsoft went to the lengths they did,” Stewart said. “That they are intercepting or trying to intercept millions of malicious requests while still allowing service to operate is unprecedented, sort of like they’re acting as ‘the great firewall of Microsoft.’ It’s not the sinkholing of these subdomains that’s novel, it’s that they’ve injected themselves legally between this service in China and its users. Handled responsibly, it could be a good thing.”
WILL THE REAL JOHN DOE PLEASE STEP FORWARD?
Like others before it, this latest legal salvo by Microsoft seeks to unmask individuals behind the alleged criminal activity at 3322.org. It does this using so-called “John Doe,” requests, which are legal proceedings that can enable a plaintiff or prosecutor to gather information on a number of individuals, in a bid to learn their identities and/or to prove they were parties to a conspiracy.
I asked Boscovich if Microsoft’s John Doe requests in previous targeted botnet takedowns had produced any leads. Specifically, I wanted to know if there were any updates to the John Does named in connection with its
targeting of the Kelihos spam botnet. In that case, Microsoft identified 31-year-old
Andrey N. Sabelnikov of St. Petersburg, Russia, a former system developer and project manager for Agnitum, a Russian antivirus firm.
“In the Kelihos case, we named the Russian AV…the individual that we alleged was the developer of the code for Kelihos,” Boscovich said. “We’re resolving that case now, and very shortly you’ll hear a statement that will be coming out.”
Shortly after that story broke, Sabelnikov vehemently refuted Microsoft’s allegations, saying he had never participated in the management of botnets or any other similar programs. But according to Boscovich, Microsoft will soon be publishing a statement that says otherwise.
“I think that once you see the statement that he agreed to that we’re going to publish in the next couple of days on the Kelihos case, I think that will put that to rest. I think we’ve been pretty accurate that when we name someone we know who they are. And there have been a lot of cases referred to law enforcement, and a lot of the evidence based upon which they’re much further along now based upon the stuff that we have done. So anybody who thinks that these things are not effective, from purely an identification of individuals behind it is concerned, they’re wrong.”
 Researchers at security vulnerability testing firm Rapid7 have added a new module to the company’s free Metasploit framework that allows users to successfully attack the vulnerability on Internet Explorer versions 7, 8 and 9 on Windows XP, Vista and 7.
Researchers at security vulnerability testing firm Rapid7 have added a new module to the company’s free Metasploit framework that allows users to successfully attack the vulnerability on Internet Explorer versions 7, 8 and 9 on Windows XP, Vista and 7. Researchers at security vulnerability testing firm Rapid7 have added a new module to the company’s free Metasploit framework that allows users to successfully attack the vulnerability on Internet Explorer versions 7, 8 and 9 on Windows XP, Vista and 7.
Researchers at security vulnerability testing firm Rapid7 have added a new module to the company’s free Metasploit framework that allows users to successfully attack the vulnerability on Internet Explorer versions 7, 8 and 9 on Windows XP, Vista and 7.