Cyberheist Smokescreen: Email, Phone, SMS Floods
It was early October 2011, and I was on the treadmill checking email from my phone when I noticed several hundred new messages had arrived since I last looked at my Gmail inbox just 20 minutes earlier. I didn’t know it at the time, but my account was being used to beta test a private service now offered openly in the criminal underground that can be hired to create highly disruptive floods of junk email, text messages and phone calls.
Many businesses request some kind of confirmation from their bank whenever high-dollar transfers are initiated. These confirmations may be sent via text message or email, or the business may ask their bank to call them to verify requested transfers. The attack that hit my inbox was part of an offering that crooks can hire to flood each medium of communication, thereby preventing a targeted business from ever receiving or finding alerts from their bank.
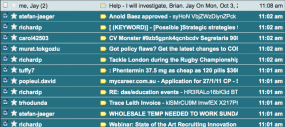 Shortly after the email barrage began, I fired off a note toGoogle‘s public relations folks, asking for advice and assistance. Thankfully, my phone line was not a subject of the attack, and I was able to communicate what I was seeing to Google’s team. They worked to fight the attack for the better part of that day, during which time my inbox received tens of thousands of emails, burying hundreds of legitimate emails in page after page of junk messages (in the screen shot above, the note to Google spokesman Jay Nancarrow is at the top of the junk message pile).
Shortly after the email barrage began, I fired off a note toGoogle‘s public relations folks, asking for advice and assistance. Thankfully, my phone line was not a subject of the attack, and I was able to communicate what I was seeing to Google’s team. They worked to fight the attack for the better part of that day, during which time my inbox received tens of thousands of emails, burying hundreds of legitimate emails in page after page of junk messages (in the screen shot above, the note to Google spokesman Jay Nancarrow is at the top of the junk message pile).
What was most surprising about these messages was that many of them contained fairly spammy subject lines that should have been easily caught by Google’s junk mail filters. Each junk message contained nothing but pages full of garbled letters and numbers; the text of each missive resembled an encrypted message.
Google’s engineers managed to block a majority of the junk messages after about six hours, but the company declined to talk about what caused the attack to succeed. It took many more hours to sift through the junk messages to fish out the ones I wanted.
“This isn’t about a hole in Gmail or an exploit — it’s more a matter of spam dynamics and what may be able to get through more easily under certain circumstances,” Nancarrow said. “As a result, we can’t provide specifics that could aid spammers in trying new campaigns.”
About a week after the attack, I was lurking on a relatively new cybercrime forum when I stumbled across an automated email flood service offered by one of the founders of the forum. The ad for this service included screenshots of a flooded Gmail inbox that looked exactly like the attack that hit my Gmail address.
The ad read, in part:
Many businesses request some kind of confirmation from their bank whenever high-dollar transfers are initiated. These confirmations may be sent via text message or email, or the business may ask their bank to call them to verify requested transfers. The attack that hit my inbox was part of an offering that crooks can hire to flood each medium of communication, thereby preventing a targeted business from ever receiving or finding alerts from their bank.
 Shortly after the email barrage began, I fired off a note toGoogle‘s public relations folks, asking for advice and assistance. Thankfully, my phone line was not a subject of the attack, and I was able to communicate what I was seeing to Google’s team. They worked to fight the attack for the better part of that day, during which time my inbox received tens of thousands of emails, burying hundreds of legitimate emails in page after page of junk messages (in the screen shot above, the note to Google spokesman Jay Nancarrow is at the top of the junk message pile).
Shortly after the email barrage began, I fired off a note toGoogle‘s public relations folks, asking for advice and assistance. Thankfully, my phone line was not a subject of the attack, and I was able to communicate what I was seeing to Google’s team. They worked to fight the attack for the better part of that day, during which time my inbox received tens of thousands of emails, burying hundreds of legitimate emails in page after page of junk messages (in the screen shot above, the note to Google spokesman Jay Nancarrow is at the top of the junk message pile).What was most surprising about these messages was that many of them contained fairly spammy subject lines that should have been easily caught by Google’s junk mail filters. Each junk message contained nothing but pages full of garbled letters and numbers; the text of each missive resembled an encrypted message.
Google’s engineers managed to block a majority of the junk messages after about six hours, but the company declined to talk about what caused the attack to succeed. It took many more hours to sift through the junk messages to fish out the ones I wanted.
“This isn’t about a hole in Gmail or an exploit — it’s more a matter of spam dynamics and what may be able to get through more easily under certain circumstances,” Nancarrow said. “As a result, we can’t provide specifics that could aid spammers in trying new campaigns.”
About a week after the attack, I was lurking on a relatively new cybercrime forum when I stumbled across an automated email flood service offered by one of the founders of the forum. The ad for this service included screenshots of a flooded Gmail inbox that looked exactly like the attack that hit my Gmail address.
The ad read, in part:
Used mostly in private for myself and now offered to the respected public.The same seller has recently added some new offerings since debuting that email bomb service, including an SMS and call flooding system. The ads for those services read:
Spam using bots, having decent SMTP accounts.
Doing email floods using bots. Complete randomization of the letter, so the user could not block the flood by the signatures.
Flooder is capable of the following functionality:
Huge wave of emails is being instantly sent to the victim. (depending on the server load and amount of emails to be flooded)
Delivery rate of 60-65% — depending on the SMTP servers.
Limit for flooding single email account on this server is 100,000 emails.
Plan – Children – 25,000 emails — $25
Plan – Medium – 50,000 emails — $40
Plan – Hard – 75,000 emails — $55
Plan – Monster – 100,000 emails — $70
NEW!!! Call Flood and mass sending SMS service!It’s alarming how easily and cheaply one can rent automated services capable of putting a small organization out of business for several days. A distributed denial of service (DDoS) attack on a company’s Web site would only increase the total cost of attack by about $50 a day, and there are a glut of DDoS services for hire these days.
Flood the phone – a great way to block the work of any business associated with a telephone number into which the flood attack. The victim, during the whole period flood, receives countless number of incoming calls. When victim answer the phone, it makes system reset, and immediately call back. This happens all time the flood attack activated. This action completely block the phone, so nobody can get through on the phone of the victim.
Flooding one or more phone numbers (any operator, any country):
1 hour = $1.5 (per number)
1 day = $ 20 (per number)
SMS mass sending:
100 SMS – $ 5
1000 SMS – $ 15
rtechinsane,icodesource,SEO,SEO Tips,SEO Backlinks,SEO content,SEO tricks,SEO Engine,codes,gadgets,iphones,ipad,4G phones,geeks,reviews,database,DBMS,


0 comments:
Post a Comment