EU to Banks: Assume All PCs Are Infected
An agency of the European Union created to improve network and data security is offering some blunt, timely and refreshing advice for financial institutions as they try to secure the online banking channel: “Assume all PCs are infected.”
The unusually frank perspective comes from the European Network and Information Security Agency, in response to a recent “High Roller” report (PDF) by McAfee and Guardian Analytics on sophisticated, automated malicious software strains that are increasingly targeting high-balance bank accounts. The report detailed how thieves using custom versions of the ZeuS and SpyEye Trojans have built automated, cloud-based systems capable of defeating multiple layers of security, including hardware tokens, one-time transaction codes, even smartcard readers. These malware variants can be set up to automatically initiate transfers to vetted money mule or prepaid accounts, just as soon as the victim logs in to his account.
“Many online banking systems….work based on the assumption that the customer’s PC is not infected,” ENISA wrote in an advisory issued on Thursday. “Given the current state of PC security, this assumption is dangerous. Banks should instead assume that PCs are infected, and still take steps to protect customers from fraudulent transactions.”
ENISA cited as an example the heavy reliance on passwords + basic two-factor authentication — such as tokens. Check the Target: Small Businesses category for a number of stories in which thieves bypassed these schemes.
“A basic two factor authentication does not prevent man-in-the-middle or man-in-the-browser attacks on transactions,” the alert stated. “Therefore, it is important to cross-check with the user the value and destination of certain transactions, via a trusted channel, on a trusted device (e.g., an SMS, a telephone call, a standalone smartcard reader with screen). Even smartphones could be used here, provided smartphone security holds up.”
ENISA further admonishes banks not to take smartphone security for granted, and that additional security measures will be needed to shore up security in the mobile space (for example, in a veiled reference to Google’s Android platform, they call for more “vetted appstores”).
No doubt security is a constantly moving target; it is necessarily reactive and therefore lags behind new methods adopted by cybercriminals. But from my perspective, the advisory highlights a fundamental reality gap between threat perception and security practice in the banking sector today.
My experience on this matter is limited mostly to the situation in the United States, where many financial institutions seem to pay lip service to security. Many simply urge customers to follow security advice that is increasingly quaint and irrelevant: Use firewall and antivirus software; don’t respond to phishing emails; pick complex passwords and change your password often.
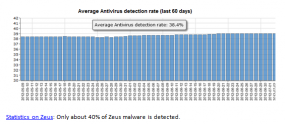
What is almost never mentioned is that all of these security procedures amount to nothing if the customer’s system is already compromised by a powerful banking Trojan like ZeuS or SpyEye. ENISA’s advisory is accompanied by a graphic showing that only about 38 percent of ZeuS malware is detected by antivirus software; that data, taken from ZeuSTracker, is slightly higher than the average I found in a similar analysis over nearly the exact same time period as the ZueSTracker sample. As I told a reader recently, I’m not saying antivirus software is completely useless, just that users should behave as though it is.
Perhaps some banks here in the U.S. already operate under the assumption that all customer PCs are compromised. But if so, I have yet to see a financial institution willing to communicate that to their customers. Larger financial institutions realize huge cost savings from having customers bank online, and are wary of doing anything to spook customers away from this medium. Smaller institutions may not realize such savings, but offer ebanking because their customers have come to expect it.
In any case, ENISA’s advisory resonated with me because I have long urged online banking customers to assume that their PCs are compromised, and to use a Live CD approach when banking online. This is more of a “must” for small businesses banking online, since — unlike consumers, who enjoy legal protection from financial losses due to cybercrime — U.S. companies of all sizes have no such guarantee when cyberheists strike.
It is true that many U.S. banks are starting to adopt promising technologies and approaches that seek to more accurately identify activity that typically precedes a cyberheist. Other banks are turning to solutions that try to create more trusted and exclusive modes of communication between financial institutions and their customers.
But this adoption process is spotty at best. In a number of upcoming stories, I’ll show showcase a series of recent cyberheists in which small businesses victims banked at institutions that continue to allow the transfer of hundreds of thousands of dollars of their customers’ money, while requiring nothing besides a simple username and password.
ENISA’s advice is all the more relevant because it is frequently difficult for customers to “shop around” for banks with the best security, beyond inquiring about customer-facing security precautions such as tokens or dual authorization: For better or worse, most financial institutions are reluctant to talk about what they may be doing to protect customers.
The “High Roller” report from McAfee and Guardian Analytics highlights a sophisticated threat that has mainly targeted European customers, but which has recently been spotted being used against high-dollar targets at U.S. banks. Perhaps one reason these particular automated attacks have been slow to target U.S. customers is the relative uniformity and low number of financial institutions in Europe, South America and other regions, in comparison to the United States. For example, the United Kingdom has only a handful of financial institutions servicing commercial and retail customers, whereas in the United States, there are more than 7,000 financial institutions.
Of course, it is not enough to fight this problem by constantly reacting to the latest malware tactics. I have long believed that although the cybercrime underground is expanding each day, much of it is run by a fairly small, loose-knit, and innovative group of hackers. That’s why I was gratified to see ENISA calling for a more coordinated response to fighting cybercriminals and their infrastructure.
Many skeptics counter that cybercrime is a whac-a-mole problem, and that as soon as you take out one prominent cybercriminal mastermind, another will rise up to take his place. This belief seems to stem from an understandable but misguided belief that the underground is a highly structured organization akin to the traditional mafia. To my mind, nothing could be further from the truth: Most of these guys can be best described as taking part in disorganized cybercrime. That is to say, they are a confederation of independent contractors who work together because it is of mutual financial benefit. The key here is that there is no loyalty in these alliances, and when one party gets arrested or disappears, it has an immediate and measurable impact on his peers.
Having spent an untold number of hours on countless underground forums, it seems to me that many of the same characters run the same sections on multiple fraud forms. As a result, targeting just a few dozen individuals — as opposed to going after a group of people engaged in a specific forum or cyberattack or crime — could have a disproportionate effect on overall cybercrime levels and losses. This was largely the conclusion of a study released last month in the U.K., called Measuring the Costs of Cybercrime (PDF).
If you run a small or mid-sized business, consider doing your banking from a Live CD. I’ve published some instructions at this link that can have you running Puppy Linux from a CD within minutes. Puppy is extremely lightweight (it fits on a regular CD), boots very quickly, and supports most hardware.
The unusually frank perspective comes from the European Network and Information Security Agency, in response to a recent “High Roller” report (PDF) by McAfee and Guardian Analytics on sophisticated, automated malicious software strains that are increasingly targeting high-balance bank accounts. The report detailed how thieves using custom versions of the ZeuS and SpyEye Trojans have built automated, cloud-based systems capable of defeating multiple layers of security, including hardware tokens, one-time transaction codes, even smartcard readers. These malware variants can be set up to automatically initiate transfers to vetted money mule or prepaid accounts, just as soon as the victim logs in to his account.
“Many online banking systems….work based on the assumption that the customer’s PC is not infected,” ENISA wrote in an advisory issued on Thursday. “Given the current state of PC security, this assumption is dangerous. Banks should instead assume that PCs are infected, and still take steps to protect customers from fraudulent transactions.”
ENISA cited as an example the heavy reliance on passwords + basic two-factor authentication — such as tokens. Check the Target: Small Businesses category for a number of stories in which thieves bypassed these schemes.
“A basic two factor authentication does not prevent man-in-the-middle or man-in-the-browser attacks on transactions,” the alert stated. “Therefore, it is important to cross-check with the user the value and destination of certain transactions, via a trusted channel, on a trusted device (e.g., an SMS, a telephone call, a standalone smartcard reader with screen). Even smartphones could be used here, provided smartphone security holds up.”
ENISA further admonishes banks not to take smartphone security for granted, and that additional security measures will be needed to shore up security in the mobile space (for example, in a veiled reference to Google’s Android platform, they call for more “vetted appstores”).
No doubt security is a constantly moving target; it is necessarily reactive and therefore lags behind new methods adopted by cybercriminals. But from my perspective, the advisory highlights a fundamental reality gap between threat perception and security practice in the banking sector today.
My experience on this matter is limited mostly to the situation in the United States, where many financial institutions seem to pay lip service to security. Many simply urge customers to follow security advice that is increasingly quaint and irrelevant: Use firewall and antivirus software; don’t respond to phishing emails; pick complex passwords and change your password often.
What is almost never mentioned is that all of these security procedures amount to nothing if the customer’s system is already compromised by a powerful banking Trojan like ZeuS or SpyEye. ENISA’s advisory is accompanied by a graphic showing that only about 38 percent of ZeuS malware is detected by antivirus software; that data, taken from ZeuSTracker, is slightly higher than the average I found in a similar analysis over nearly the exact same time period as the ZueSTracker sample. As I told a reader recently, I’m not saying antivirus software is completely useless, just that users should behave as though it is.
Perhaps some banks here in the U.S. already operate under the assumption that all customer PCs are compromised. But if so, I have yet to see a financial institution willing to communicate that to their customers. Larger financial institutions realize huge cost savings from having customers bank online, and are wary of doing anything to spook customers away from this medium. Smaller institutions may not realize such savings, but offer ebanking because their customers have come to expect it.
In any case, ENISA’s advisory resonated with me because I have long urged online banking customers to assume that their PCs are compromised, and to use a Live CD approach when banking online. This is more of a “must” for small businesses banking online, since — unlike consumers, who enjoy legal protection from financial losses due to cybercrime — U.S. companies of all sizes have no such guarantee when cyberheists strike.
It is true that many U.S. banks are starting to adopt promising technologies and approaches that seek to more accurately identify activity that typically precedes a cyberheist. Other banks are turning to solutions that try to create more trusted and exclusive modes of communication between financial institutions and their customers.
But this adoption process is spotty at best. In a number of upcoming stories, I’ll show showcase a series of recent cyberheists in which small businesses victims banked at institutions that continue to allow the transfer of hundreds of thousands of dollars of their customers’ money, while requiring nothing besides a simple username and password.
ENISA’s advice is all the more relevant because it is frequently difficult for customers to “shop around” for banks with the best security, beyond inquiring about customer-facing security precautions such as tokens or dual authorization: For better or worse, most financial institutions are reluctant to talk about what they may be doing to protect customers.
The “High Roller” report from McAfee and Guardian Analytics highlights a sophisticated threat that has mainly targeted European customers, but which has recently been spotted being used against high-dollar targets at U.S. banks. Perhaps one reason these particular automated attacks have been slow to target U.S. customers is the relative uniformity and low number of financial institutions in Europe, South America and other regions, in comparison to the United States. For example, the United Kingdom has only a handful of financial institutions servicing commercial and retail customers, whereas in the United States, there are more than 7,000 financial institutions.
Of course, it is not enough to fight this problem by constantly reacting to the latest malware tactics. I have long believed that although the cybercrime underground is expanding each day, much of it is run by a fairly small, loose-knit, and innovative group of hackers. That’s why I was gratified to see ENISA calling for a more coordinated response to fighting cybercriminals and their infrastructure.
Many skeptics counter that cybercrime is a whac-a-mole problem, and that as soon as you take out one prominent cybercriminal mastermind, another will rise up to take his place. This belief seems to stem from an understandable but misguided belief that the underground is a highly structured organization akin to the traditional mafia. To my mind, nothing could be further from the truth: Most of these guys can be best described as taking part in disorganized cybercrime. That is to say, they are a confederation of independent contractors who work together because it is of mutual financial benefit. The key here is that there is no loyalty in these alliances, and when one party gets arrested or disappears, it has an immediate and measurable impact on his peers.
Having spent an untold number of hours on countless underground forums, it seems to me that many of the same characters run the same sections on multiple fraud forms. As a result, targeting just a few dozen individuals — as opposed to going after a group of people engaged in a specific forum or cyberattack or crime — could have a disproportionate effect on overall cybercrime levels and losses. This was largely the conclusion of a study released last month in the U.K., called Measuring the Costs of Cybercrime (PDF).
If you run a small or mid-sized business, consider doing your banking from a Live CD. I’ve published some instructions at this link that can have you running Puppy Linux from a CD within minutes. Puppy is extremely lightweight (it fits on a regular CD), boots very quickly, and supports most hardware.
Have you seen:
Banking on a Live CD…An investigative series I’ve been writing over the past three years about organized cyber crime gangs using malware to steal millions of dollars from small to mid-sized organizations has generated more than a few responses from business owners concerned about how best to protect themselves from this type of fraud. I said this nearly three years ago, and it remains true: The simplest, most cost-effective answer I know of? Don’t use Microsoft Windows when accessing your bank account online.rtechinsane,icodesource,SEO,SEO Tips,SEO Backlinks,SEO content,SEO tricks,SEO Engine,codes,gadgets,iphones,ipad,4G phones,geeks,reviews,database,DBMS,


0 comments:
Post a Comment