Inside the Grum Botnet
KrebsOnSecurity has obtained an exclusive look inside the back-end operations of the recently-destroyed Grum spam botnet. It appears that this crime machine was larger and more complex than many experts had imagined. It also looks like my previous research into the identity of the Grum botmaster was right on target.
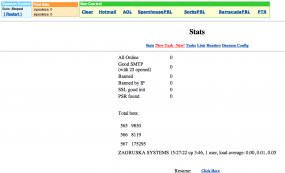 The “Stats” page from a Grum botnet control panel show more than 193,000 systems were infected with the malware.
A source in the ISP community who asked to remain anonymous shared a copy of a Web server installation that was used as a controller for the Grum botnet. That controller contained several years’ worth of data on the botnet’s operations, as well as detailed stats on the spam machine’s size just prior to its takedown.
The “Stats” page from a Grum botnet control panel show more than 193,000 systems were infected with the malware.
A source in the ISP community who asked to remain anonymous shared a copy of a Web server installation that was used as a controller for the Grum botnet. That controller contained several years’ worth of data on the botnet’s operations, as well as detailed stats on the spam machine’s size just prior to its takedown.
At the time of Grum’s demise in mid-July 2012, it was responsible for sending roughly one in every six spams delivered worldwide, and capable of blasting 18 billion spam emails per day. Anti-spam activists at Spamhaus.org estimated that there were about 136,000 Internet addresses seen sending spam for Grum.
But according to the database maintained on this Grum control server prior to its disconnection in mid-July, more than 193,000 systems were infected with one of three versions of the Grum code, malware that turned host systems into spam-spewing zombies. The system seems to have kept track of infected machines not by Internet address but with a unique identifier for each PC, although it’s not immediately clear how the Grum botnet system derived or verified those identifying fingerprints.
The Web interface used to control the botnet was called “Zagruska Systems,” (“zagruska” is a transliteration of the Russian word “загрузка,” which means “download”). The HTML code on the server includes the message “Spam Service Coded by -= ( Spiderman).”
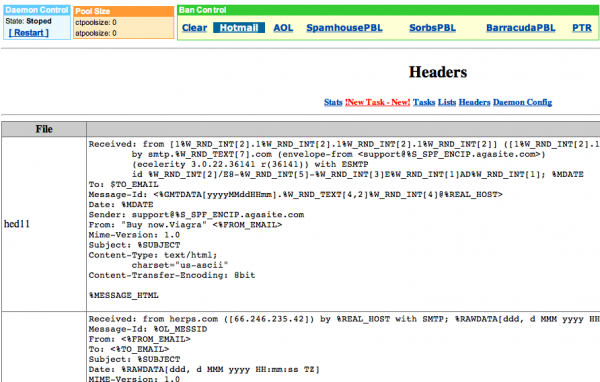
The password used to administer the botnet’s Web-based interface was “a28fe103a93d6705d1ce6720dbeb5779″; that’s an MD5 hash of the password “megerasss”. Interestingly, this master password contains the name Gera, which I determined in an earlier investigative story was the nickname used by the Grum botmaster. The name Gera also is used as a title for one of several classes of forged email headers that the botnet had available to send junk mail; other titles for falsified header types included the names “Chase,” “eBay” and “Wachovia,” suggesting a possible phishing angle.
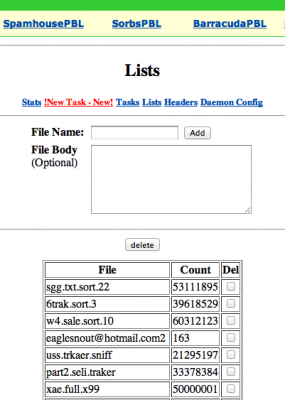
This Grum control server also hosted some unbelievably large email address lists — more than 350 GB worth in all. There were dozens of separate email address lists on the Grum control server, many containing between 20 million and 60 million email addresses each. I was unable to determine how many unique or active email addresses were contained in these files, but a quick tally of 60 different address list files found in one directory on the server showed that they contained more than 2.3 billion addresses.
Most of the junk mail that Grum sent was for ads promoting rogue Internet pharmacies and replica watches, although there are indications that the botnet was at some point in 2011 used to distribute malware disguised as a DHL shipping notification.
Further poking around this control server revealed that it contained the customer information for more than 1.3 million orders placed at rogue Internet pharmacies between Feb. 2006 and March 2010. The order information for the online pill shops was in a folder on the system called “Rx-Partners,” suggesting they were records belonging to the pharmacy spam affiliate program by the same name. The database includes order numbers, dates, the type of drug purchased, strength, quantity, price, customer country, and email address, among other information. I’ll have more details on this aspect of the Grum data trove in a future post.
 The “Stats” page from a Grum botnet control panel show more than 193,000 systems were infected with the malware.
The “Stats” page from a Grum botnet control panel show more than 193,000 systems were infected with the malware.At the time of Grum’s demise in mid-July 2012, it was responsible for sending roughly one in every six spams delivered worldwide, and capable of blasting 18 billion spam emails per day. Anti-spam activists at Spamhaus.org estimated that there were about 136,000 Internet addresses seen sending spam for Grum.
But according to the database maintained on this Grum control server prior to its disconnection in mid-July, more than 193,000 systems were infected with one of three versions of the Grum code, malware that turned host systems into spam-spewing zombies. The system seems to have kept track of infected machines not by Internet address but with a unique identifier for each PC, although it’s not immediately clear how the Grum botnet system derived or verified those identifying fingerprints.
The Web interface used to control the botnet was called “Zagruska Systems,” (“zagruska” is a transliteration of the Russian word “загрузка,” which means “download”). The HTML code on the server includes the message “Spam Service Coded by -= ( Spiderman).”
The password used to administer the botnet’s Web-based interface was “a28fe103a93d6705d1ce6720dbeb5779″; that’s an MD5 hash of the password “megerasss”. Interestingly, this master password contains the name Gera, which I determined in an earlier investigative story was the nickname used by the Grum botmaster. The name Gera also is used as a title for one of several classes of forged email headers that the botnet had available to send junk mail; other titles for falsified header types included the names “Chase,” “eBay” and “Wachovia,” suggesting a possible phishing angle.
This Grum control server also hosted some unbelievably large email address lists — more than 350 GB worth in all. There were dozens of separate email address lists on the Grum control server, many containing between 20 million and 60 million email addresses each. I was unable to determine how many unique or active email addresses were contained in these files, but a quick tally of 60 different address list files found in one directory on the server showed that they contained more than 2.3 billion addresses.
Most of the junk mail that Grum sent was for ads promoting rogue Internet pharmacies and replica watches, although there are indications that the botnet was at some point in 2011 used to distribute malware disguised as a DHL shipping notification.
Further poking around this control server revealed that it contained the customer information for more than 1.3 million orders placed at rogue Internet pharmacies between Feb. 2006 and March 2010. The order information for the online pill shops was in a folder on the system called “Rx-Partners,” suggesting they were records belonging to the pharmacy spam affiliate program by the same name. The database includes order numbers, dates, the type of drug purchased, strength, quantity, price, customer country, and email address, among other information. I’ll have more details on this aspect of the Grum data trove in a future post.


0 comments:
Post a Comment